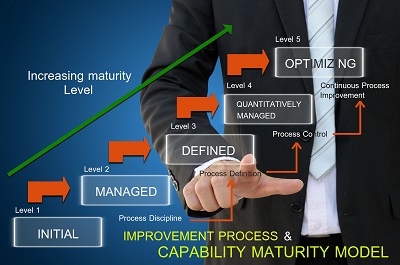
Assessment Overview
IT maturity Assessments are a good way to get a picture of your IT organization’s current state. CIO Street developed a survey organized into 12 Maturity categories that were deemed highly strategic from veteran C-level leaders with years of experience in small, medium, and large organizations. This assessment should be used as a reference guide not as a report card on how well or poorly an IT organization functions. Every business is different; therefore, the IT requirements will also be different and cannot accurately be judged by a single model of conformity. That being said, we believe our survey will help an organization recognize possible areas for improvement and assist in forming a strategic plan for the future.
For ease of use, CIO Street has 2 assessments available. A quick 2 question per Maturity category survey that provides an overview of an IT organizations current state or a complete 77 question survey that provides a more accurate IT maturity state. If you complete the short survey and are interested in a more in-depth assessment, fill free to open the comprehensive questionnaire and complete the remaining questions.
Once you complete the survey, you will receive immediate results and a few suggestions for improvement. Have fun!
Please complete this form to access the Full Survey
: Registered Guests enter Email and Phone
(We promise not to harass you with uninvited solicitations or share your data with a 3rd party)
IT Maturity Survey - Short Version
Category I - User Support (including 3rd party vendor support)
1. Does your organization provide 24/7 support via voice, email, and on-line portal?
2. Would you rank your organization’s overall user support as above average?
3. Does your organization provide a user support ticketing application available via email, on-line portal or using a mobile device?
4. Does your organization provide a self-service password reset system?
5. Does your organization provide an on-line FAQ for common service problems?
6. Does your organization monitor user support and proactively eliminate common support causes?
Category II - Vision and Planning
1. Does your IT organization develop and follow a strategic plan?
2. Does you IT Organization develop and follow an annual budget?
3. Does your IT organization develop and follow a formal mobile device and access strategy?
4. Does your IT organization have a formal data and business intelligence strategic plan?
5. Does your IT organization have a documented artificial intelligence strategic plan?
Category III - People (including long term 3rd party contractors)
1. Is your IT organization staffed appropriately?
2. Does your IT organization provide training and skill development for its team members?
3. Does each position in your IT organization have a clearly defined job description with essential duties, responsibilities, and performance expectations provided for each team member?
4. Does your IT organization provide its team members with a clear path for career development?
5. Does you IT organization have a formal succession plan for key positions?
Category IV - Network Connectivity
1. Does your organization provide fast reliable network connectivity between physical locations/cloud, and the Internet?
2. Does your organization use multiple vendors and network connections between locations/cloud and the Internet for redundancy?
3. Does your organization provide fast reliable mobile connectivity for all users?
4. Does your IT organization monitor network connectivity 24/7?
5. Does your IT organization have a formal network incident response plan?
6. Does your organization have an automated network intrusion detection system with incident alerting?
7. Does your organization provide a separate and isolated network connection to the Internet for guests and visitors?
8. Does your IT organization have automated monitoring of unauthorized device connectivity?
Category V - User Devices (including 3rd party vendor devices)
1. Does your organization provide the capability to use mobile devices for primary work requirements?
2. Does your organization automatically encrypt all data stored on user devices?
3. Does your organization provide pre-configured desktops, laptops, and/or tablets that have been appropriately imaged for each user?
4. Does your organization automatically back-up user data where appropriate?
5. Does your organization have a formalized client device replacement plan?
6. Are any of the user devices within the organization more than 5 years in age?
Category VI - Enterprise Hardware (including 3rd party vendor supplied hardware)
1. Does your organization use multiple data centers and/or cloud computing environments with high-availability failover capabilities?
2. Does your IT organization use and regularly test appropriate backup and recovery processes?
3. Does your IT organization have a formalized application/systems incident response plan?
4.Does your organization use and regularly test a formalized and appropriate disaster recovery/business continuity plan?
5. Are any of the hardware devices or cloud environment for enterprise systems more than 5 years in age?
Category VII - Enterprise Software (including 3rd party vendor supplied software)
1. Are all of the enterprise systems (Finance, HR, Payroll, email, etc.) appropriate and responsive for all of the organization’s users?
2. Has any of the organization’s enterprise software gone more than a year without an update?
3. Are all of the organization’s enterprise applications available remotely and via mobile device?
Category VIII - Security and Governance (including 3rd party vendors)
1. Does your IT organization have formalized policies and procedures for network and application access?
2. Does your IT organization automatically load and update user and enterprise hardware with antivirus software?
3. Does your IT organization use a tiered approval system to grant access to the network and applications?
4. Does your IT organization perform a user access review at least twice a year?
5. Does your IT organization use a multi-factor form of identifying users before granting access to networks and applications?
6. Is data encrypted at rest for all enterprise systems?
7. Does your IT organization continually develop and test for security incidents?
8. Does you IT organization automatically implement security and operating system updates?
9. Does your IT organization provide an email gateway for removing spam??
10. Does your IT organization develop and practice a cloud security policy and procedure?
11. Does your IT organization use an email testing and forwarding system to guard against malware?
12. Does your IT organization regularly perform network and systems penetration tests from multiple vendors?
13. Does your IT organization regularly perform user phishing tests?
14. Does your IT organization provide user security training on a regular basis?
15. Does your IT organization provide warnings of possible cyber security threats to end-users?
16. Does your organization use a data traffic monitoring system to provide early warnings of anomalous access and data movement?
17. Does your IT organization provide tools for reporting any required regulatory system/application security and change management policies, procedure, and monitoring?
Category IX - Change Management (including 3rd party vendor changes)
1. Does your IT organization develop and use formal change management policies and procedures?
2. Does your IT organization require testing of all changes prior to implementation?
3. Does your IT organization require a multi-tiered approval of system and software changes?
4. Does your IT organization review system logs for unauthorized changes on a regular basis?
Category X - Project Management (including 3rd party vendor implementations)
1. Does your IT organization develop and practice formal Project Management Office policies and guidelines similar to the PMBOK?
2. Does a majority of IT projects within your organization originate from the business or IT?
3. Does your IT organization maintain a project portfolio that is approved by all appropriate stake holders?
4. Does your IT organization always provide project oversight including 3rd party vendor application and systems implementations?
5. Does your IT organization have formal guidelines and procedures for project scope changes, completion delays, and cost overruns?
Category XI - Software Development (including 3rd party vendor development)
1. Does your IT organization develop and practice formal software development and testing policies and procedures?
2. Are custom development and integration projects always tested at the unit and end-user level before implementation?
3. Does your IT organization provide formal documentation of all custom software development or integration projects?
4. Does your IT organization use an agile model for software development and integration efforts?
5. Does your IT organization use a mobile-first approach to software and application design?
6. Does your IT organization use a DevOps framework for development and integration endeavors?
7. Does your IT organization always incorporate security, user access, and change management policies into development/integration projects?
8. Does your IT organization use templates, standards, and common tools for every development/integration project?
Category XII - Decision Support (including 3rd party vendor supplied data services)
1. Does your IT organization develop and maintain a map of all available data resources within the organization?
2. Does your IT organization provide adequate decision support resources for operational performance?
3. Does your IT organization provide end user access to centralized data for easy self-service reporting?
4. Does your IT organization provide centralized dashboards for operational performance monitoring?
5. Does your IT organization provide tools for performing what-if scenarios using data analytics?
Complete this form and immediately see your results!
: Registered Guests enter Email and Phone
(We promise not to harass you with uninvited solicitations or share your data with a 3rd party)
